Exploring OpenChain: From License Compliance to Security Assurance
The OpenChain project was first founded in 2016 by the Linux Foundation, they aim to build confidence in the open-source software supply chain. Their first published standard is known as OpenChain ISO/IEC 5230 which focuses on license compliance, training, the processes and management of using open-source software. This blog explores how the OpenChain ISO/IEC 18974 Security Assurance standard is different from the original OpenChain ISO/IEC 5230 License Compliance standard.
What is the new OpenChain standard?
OpenChain ISO/IEC 18974 is the newest OpenChain standard which focuses on security assurance when using open-source software. As OpenChain ISO/IEC 5230 has a strong focus on supply-chain security, the topic was discussed and mentioned frequently. Subsequently, the decision was made to create a separate standard to focus solely on security concerns in open-source software supply chains. This led to the development of OpenChain ISO/IEC 18974 which provides guidelines and requirements for security assurance. This includes tracking components with SBOMs and identifying vulnerabilities in software using publicly published information.
Whereas OpenChain license compliance ISO/IEC 5230 requires organisations to implement processes that track open-source software usage from acquisition to deployment. This includes tracking how and where each component and license is being used and checking its usage following the set policies. By doing so, organisations can see exactly what is being used in their supply chain, reducing the risk of legal and reputational problems.
Why is security assurance important?
As the world becomes increasingly dependent on technology, software is being used from core national infrastructures, such as telecoms, utilities (water, gas, electricity), aviation, and defence, to smart home devices (heating, kitchen appliances, smart meters, and various other IoT devices). Therefore, it must be safe and secure. If there are vulnerabilities in a system where classified information is being stored, or in a system that holds a company together, and that vulnerability is targeted it could be detrimental or dangerous.
Open-source software is generally used due to its cost-effectiveness and flexibility, but this comes with security risks. This should be of great concern to organisations, as a security flaw could result in undesired outcomes, such as a data breach, which would severely affect a company's reputation and financial position.
Having security flaws can greatly impact an organisation, here are some of the main impacts:
1. Data Breach:
Security flaws can result in sensitive information being exposed. This can lead to the loss of personal information, financial information, company secrets, and any other confidential data. This can cause numerous financial problems for the company, legal issues and subsequently reputational issues.
The multinational consumer credit reporting agency, Equifax, had not updated a third-party patched exploit, therefore resulting in over 150 million customers' private records being compromised. The breach cost the company over $1.7 billion in total.
2. Malware attacks:
Security flaws in software could be targeted by malicious malware attacks. This could lead to data breaches and system problems.
3. Financial losses:
Security flaws in software could lead to theft. Either directly from the company, or in a roundabout way, where finance needs to cover data breaches and/or legal action.
in 2018, British Airways lost the personal information of over 400,000 staff and customers; breaching article 32 under GDPR, therefore, resulting in £20 million in fines. The information lost included bank details, names and addresses.
4. Loss of regulatory compliance:
Security flaws could result in a breach of regulatory compliance such as GDPR article 32 which requires systems and processes to protect data, or PCI DSS (Payment Card Industry Data Security Standard). This could lead to financial and legal repercussions.
5. Reputational issues:
As a result of security flaws, could damage an organisation's reputation, leading to less trust from customers or stakeholders. This lack of trust could affect the success of an organisation
In 2015 TalkTalk was hit with a cyber attack meaning that over 150,000 customers' data was leaked, and it resulted in a financial loss of £77 million. This majorly affected their reputation due to poor communication and outreach after the attack.
6. Reduction in productivity:
Security flaws can reduce productivity if time needs to be displaced to fixing down systems, or if a system is down as a result of an attack
In 2021, supermarket chain Coop in Sweden had to close over 400 stores due to a ransomware attack on another organisation's software that the chain used to operate the checkouts in their stores.
The Changing Supply Chain
The software supply chain is made up of all the components, scripts, libraries, tools and processes that are needed to build a software system. Having a formal artefact to provide information about the supply chain may show dependencies.
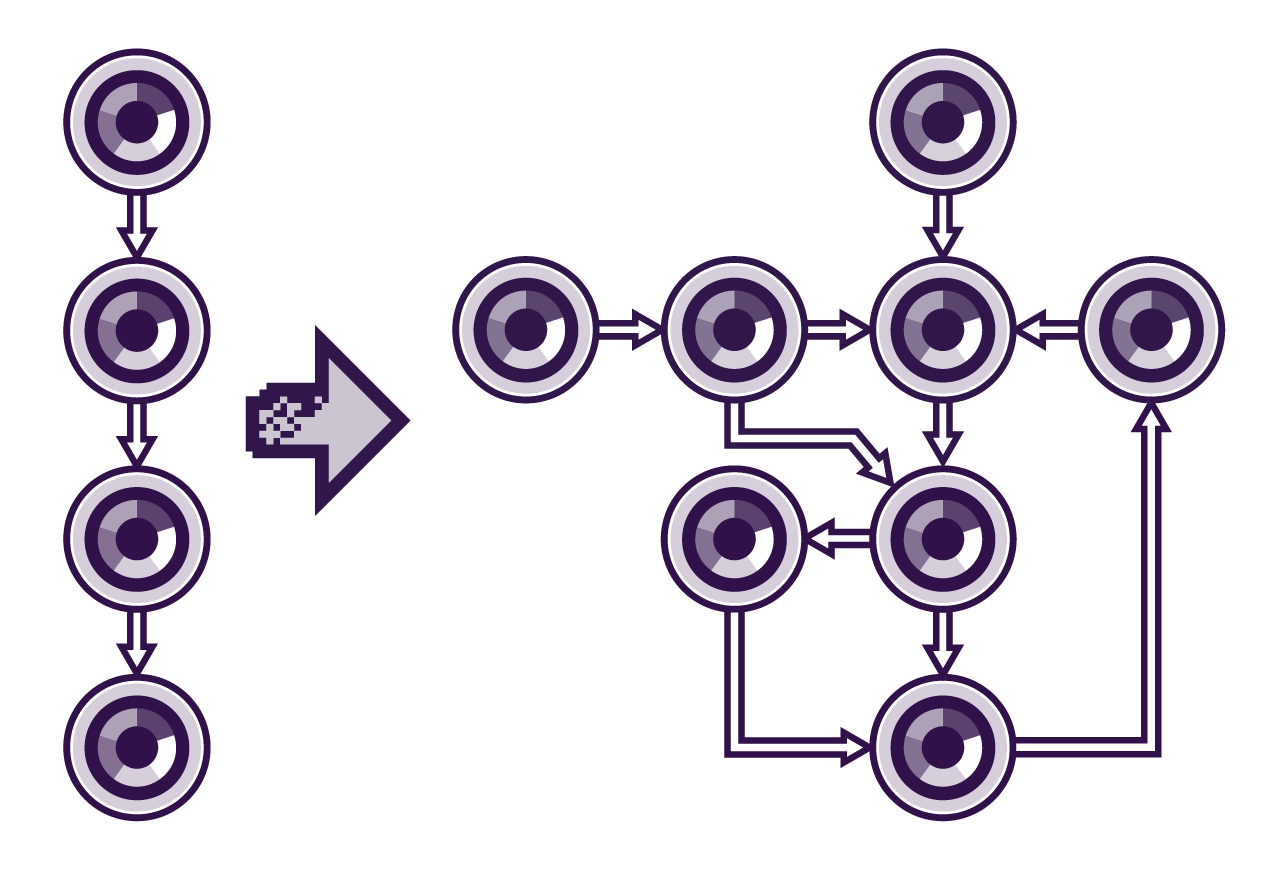
The above schematic shows the supply chains of systems are becoming less vertically integrated (as shown on the left) and more complex and growing rapidly (as shown on the right). Becoming less vertically integrated means more software components are being used from external sources, for example, this could be open-source software.
As systems become more complex and interconnected, tracking these open-source components and managing the risks that follow the growing dependency tree becomes more difficult. Therefore, there becomes a need for a system that can manage security risks before they become a problem.
As these systems are growing, there are more components and dependencies in the supply chain to track. These dependencies are constantly being updated and used by many people, increasing the risk of vulnerabilities being present in the code.
OSS components offer building blocks of value and therefore can be very popular (millions of users) meaning they are a very attractive attack vector. A vulnerability in one component would allow a vast number of potential victims.
Implementing processes for security assurance
The OpenChain security assurance standard covers:
- Where to list your security processes
- Assigning roles and responsibilities around the standard
- How to ensure the sustainability of the processes
As every organisation operates individually in different ways, there is no set method to becoming compliant, however, OpenChain has set out the goals which act as an end destination, making it easier to develop a path there.
We have been developing processes to ensure that our open-source software is secure. We've been using SBOMs (software bill of materials) to track all the components of our system. This will allow us to check for known vulnerabilities within our software. To do this we will use the GitHub Advisory Database, a useful website that lists known vulnerabilities in open-source software, it states the severity of the bug, when it was found and the version number it affects. Building processes and resources around this that can adapt to new vulnerabilities found is becoming more important.
The OpenChain ISO/IEC 18974 Standard
The OpenChain ISO/IEC 18974 standard defines the requirements that a program must satisfy to achieve security assurance. The standard defines the methods that should be used, for example having a process that checks for unknown vulnerabilities, and processes ensuring that components are being tracked with SBOMs.
On the OpenChain website, there is an OpenChain Self Certification questionnaire that you can fill out. This will give you an indication of where you currently are with open-source compliance, and what you still need to implement. There are also checklists that you can track your progress with along the way. OpenChain has official partners for third-party certification that will confirm that an organisation has achieved the OpenChain standard. There are also vendors and service providers that can help with implementation.
There are resources available with more information, such as:
- Training slides
- Playbooks - Shows how different size companies can use OpenChain
- Webinars - Wide range of relevant content from 'Getting Started with OpenChain' to 'Agile Development' and real-world examples
- Templates - Contains the reference policy template which helps apply the key requirements for open-source compliance