Cloud Adoption: Risks & Mitigations Analysis
Barry Smart was the CTO at Hymans Robertson, the largest independent firm of consultants and actuaries in the UK, between 2012-2019. He was responsible for leading the firm's technology strategy, modernising the 100 year old organisation, and transforming them through the adoption of Microsoft's Azure Cloud platform to enable them to innovate faster and produce new digital products and services.
Since 2013, endjin has been helping Hymans Robertson with their Azure adoption process. As a Financial Services organisation, they are regulated by the FCA, and as early adopters of Azure, were at the bleeding edge of storing Personally Identifiable Information (PII) in the cloud. THis meant that they were ahead of the regulator, were breaking new ground, and needed a evidence-based approach to demonstrate to the regulator that they could identify and mitigate the risks of moving to The Cloud.
Since developing this approach, we (endjin) have used it for many different customers; from global enterprises to early start-ups, in many difference sectors. It's a useful strategic tool to help you understand the the gotchas of moving to the cloud, and how you can put people, process and technical barrier in place to prevent the worse outcome from ever happening.
In this three-part series, Barry Smart describes the risk & mitigations analysis process we came up with, and explains how you can use the same process to understand the risk of your own cloud journey.
- Part 1 - Cloud Adoption: Risks & Mitigations Analysis
- Part 2 - A Deep Dive into the Swiss Cheese Model
- Part 3 - Benchmarking the Cloud against on-premise data centres
Cloud Computing: a matter of life and death?
The successful adoption of Cloud technology will become critical to the longevity of many businesses. The Cloud is the foundation of a digital revolution that is enabling innovators to bring highly disruptive business models to market that can "kill" the laggards who fail to embrace this technology. In this blog series, I explore how this "life or death" situation for businesses draws parallels with the world of health and safety and how a technique used to manage health and safety risk can be transferred to management of the risks associated with Cloud services.
The age of Cloud technology is upon us
The Cloud feels like an unstoppable force that every business is having to grapple with in some shape or form.It is enabling new business models that are having a transformational impact across a wide range of markets. For example, it has enabled companies such as Amazon, Apple and airbnb to build new business models that have had a huge disruptive impact on the retail, music industry and accommodation industries respectively.
Another challenge is that the Cloud is not standing still and it can be difficult to keep up! There are a rapidly growing range of services on offer from cloud providers.The market for "off the shelf" applications through Software as a Service (SaaS) is exploding, enabling businesses to rapidly adopt best of breed solutions in areas such as customer relationship management, accounting or project management with little or no need to invest in supporting infrastructure. This "app economy" provides new levels of agility for businesses, freeing them from the burden of having to maintain legacy business applications.
My focus is on PaaS
Whilst SaaS has an important role to play in providing "commodity" applications in a cost effective and scalable manner, I am more interested in the use of Platform as a Service (PaaS) to provide the building blocks for bespoke applications that harness the unique capabilities of the Cloud to deliver competitive advantage through disruptive business models. For example: by putting machine learning at the heart of your customer experience, or using Big Data technology to generate unforeseen value from data sets that you own as a business, or leveraging highly scalable distributed computing for intensive workloads to offer services that are faster and cheaper than your competitor.
Back in 2012, I felt that Pubic Cloud PaaS had reached a sufficient level of maturity to support a new generation of applications that could be built with less effort, be more secure and cheaper to scale. I wanted to grab this opportunity!
So the journey began. Driven by the desire to leverage PaaS, I decided that we needed to embrace the Cloud rather than to fight against it. I wanted to engage with Cloud technology on my terms, backed up with the support of the wider organisation, rather than finding that I had been swept along by it. We hear about "shadow IT" and I wanted to avoid this scenario by taking a coherent, proactive approach. But I soon found that there would be a challenges on way to achieving this objective…
Nebulous conversations
I started to explore the appetite for adopting Cloud technology across the business.By testing a cross section of stakeholders, I soon found a wide spectrum of views ranging from robust opposition ("The Cloud is too risky. We'll never be able to convince our clients to adopt it.") through indifference ("I don't see how the Cloud is relevant for our business.") to enthusiastic support ("I see big opportunities, the Cloud has to be a major part our future business."). I'm glad to say that the majority of the views fell toward the enthusiastic support end of the spectrum, but I wanted to build a greater level of consensus.
Another factor that was making the picture fuzzy for stakeholders were a number of external factors:
- High profile data leakage events - concern about the increasing cadence and magnitude of high profile incidents. For example, TalkTalk's leakage of personal data for over 150,000 customer in October 2015;
- Changes to data protection law - there was nervousness about the forthcoming changes to European Data Protection Law that could make it more onerous to place customer data on the Cloud;
- Industry specific regulation - regulators were taking an increasing interest in the Cloud. Whilst much of this was positive (for example the FCA's recent guidance consultation regarding use of Cloud services) it was clear that the regulatory landscape was likely to continue to evolve.
Getting to the point
Through these initial conversations, I discovered that the Cloud can be an emotive subject and also something that could be explored from many different angles given the specific interests or experiences of the stakeholder concerned. I was worried that I would be endlessly circling and not reaching a consensus. So I set about finding a framework that would allow me to keep the conversation focused, enabling me to focus on answering key questions such as:
- What risks are we facing by placing data, applications and other technology services in the Cloud?
- What responsibilities would we retain, and which would be passed to the Cloud provider?
- Do we have the skills, experience and capabilities to manage the risks associated with adoption of the Cloud?
- How does the overall risk profile of the Cloud compare to our current on premise data centers?
(I'll provide the answers to these questions in a future blog. For now I wanted to focus on the structured approach we took to finding the answers to these questions.)
Grabbing the attention of "C" grade executives
Whilst there are a range of comprehensive frameworks available in the public domain that assess Cloud risk, such as ENISA's cloud computing risk assessment, I felt that these were too technical for my purposes. I needed something more accessible. Ideally a single page visual model that would engage and support a short, high quality conversation with each stakeholder. It also had to be tailored to reflect the specific risks that my organisation were facing to make it relevant. Finally, I had the thought that if this visual model worked within the firm, we could ultimately share this with our clients to demonstrate the level of due diligence we had applied to our Cloud adoption and to help them gain the same level of comfort.
Taking inspiration from safety management
I took some inspiration from a previous role I had in the Energy sector where I took an active part in the adoption of guidance from the UK's Health and Safety Executive (HSE) regarding the control of major hazard risks. Central to this guidance was the concept of the "Swiss Cheese Model". It was based on a range of principles that I felt could be translated directly onto Cloud risks. They are:
- As a business, you need to understand the nature of the threats that you are dealing with and the undesired outcomes that would result should these threats not be contained;
- In order to successfully contain these threats, a range of controls (also called barriers) are required;
- These barriers fall into three broad categories:
- Physical (or technical) aspects inherent in the design and implementation of the system;
- Processes that are essential to managing risks such as regular maintenance, proactive monitoring and quality assurance;
- People related attributes such as organisational design, training or communications.
The Swiss Cheese Model postulates that major incidents tend to occur when there are concurrent failures in multiple barriers.
Why the reference to cheese?
So, you may ask: where does the term "Swiss Cheese" come from? It comes from a visualisation of the principles set out above. The figure below which illustrates this with:
- Threats, on the left;
- The undesired outcomes (that could result from these threats) on the right;
- The controls that prevent these threats becoming a reality as a series of barriers in-between (classified as physical, process and people);
- The weaknesses in controls depicted as holes in the barriers;
- The occurrence of a major incident as the pathway from the threat on the left through the concurrent holes in the barriers to realisation of the undesired outcome on the right.
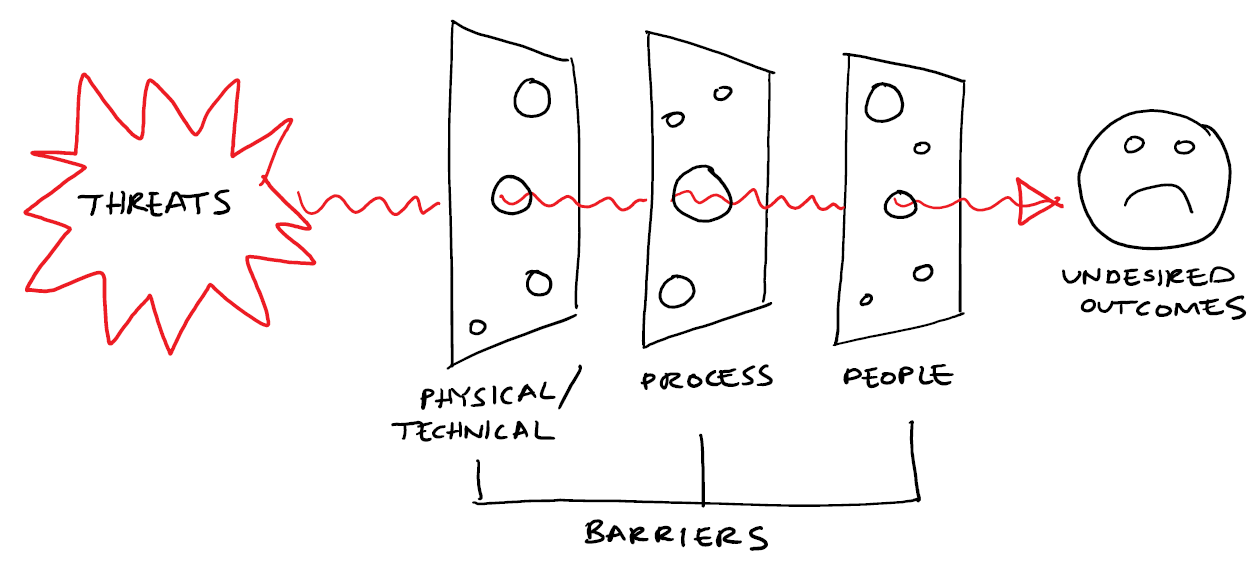
As you can see from the illustration above, the barriers appears as a slices of Swiss cheese, hence the name of this risk model!
What does the Swiss Cheese Model look like for the Cloud?
I don't believe there is a single answer. The Swiss Cheese Model is driven by a range of factors such as:
- Your business model -this will drive the specific risks that you are most concerned about to the fore, the corresponding threats that you identify and the controls (or barriers) that you feel are important to successfully contain those threats;
- The design of your risk management system -the implementation of each control is dependent on your choices as an organisation, the cloud vendor that you have chosen and the specific Cloud services on offer that you are proposing to consume.
When I developed the Swiss Cheese Model for my organisation, I had a specific use case in mind and we had also chosen our cloud provider.It still took me about 4 weeks to finalise the Swiss Cheese Model, involving many conversations with a wide range of people.The result was:
- 3 undesired outcomes that we wanted to avoid: information leakage, poor performance and poor commercials;
- 21 threats ranging from external factors such as cyber crime to internal concerns such as poor quality of coding;
- 48 barriers that we believed were critical. These were grouped into 3 categories: physical, process and people.
This is illustrated in the diagram below:
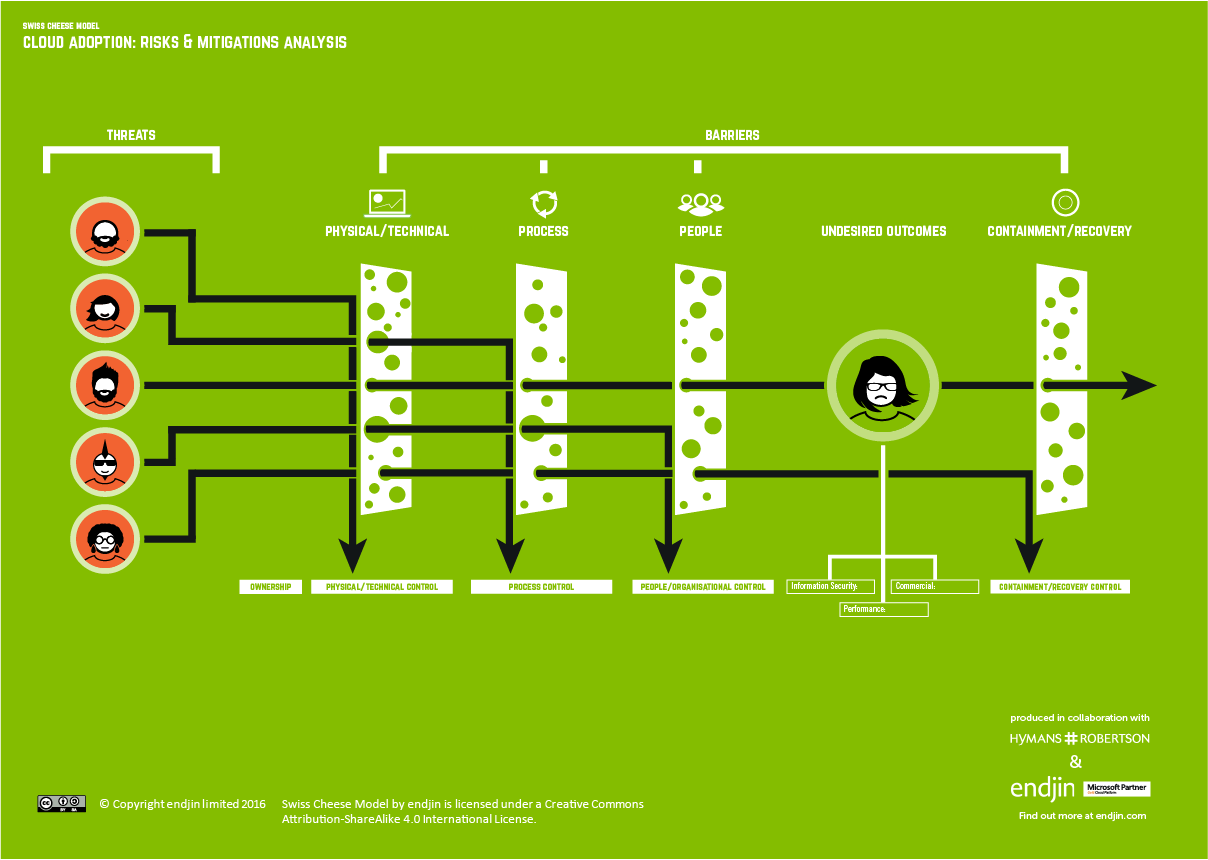
I will talk you through this model in more detail in a separate blog post.I'm sure you won't agree with it 100% -you'll spot things that I have missed, or disagree with the way that I have classified the controls or assessed the residual risk.I would be interested in your thoughts. However, I feel that the collaborative process that I took to create the model was more valuable than the end result.
This framework allowed us to benchmark the Cloud with our own on-premise data centers and conclude that, on balance, the Cloud presented a lower information security risk than on-premise for our specific use case. I will explain how we performed this benchmark and our rationale for this conclusion in a separate blog.
Taking proactive steps to strengthen our risk management
One important outcome from the process was identifying a barrier that we felt that we needed to strengthen in order to manage the threats effectively: this was an ability to encrypt sensitive data at rest within the Cloud.
We were relatively comfortable with the technical aspects of encrypting data, but were unsure how we could put in place protection of the associated keys and secrets. By encrypting the data, we realised that we would be were transferring risk and we felt there were two specific capabilities that would be required to manage this:
- Segregation of duties - for example, ensuring that only a small number of people would have access to all pieces of information required to decrypt data, but in turn, would not access to the data itself;
- Protecting secrets and keys - find a mechanism that we could protect the keys and secrets from being lost and resulting in loss of access to the encrypted data.
Armed with a clear statement of the problem we needed to solve, we worked with Endjin to run a structured experiment to demonstrate how we could encrypt sensitive data in the Cloud without introducing new risks. The details of this experiment are provided in a separate series of blogs.
Conclusion: the value is in the doing, not just the end result
We found that the process of constructing a Swiss Cheese Model from first principles, that was specific to our business model, was as valuable as the end result.It enabled us to take a holistic look at the risks, providing a focal point for the diverse range of stakeholders who were involved (software engineering, infrastructure, legal, quality assurance, information security, cyber security, finance and business continuity).
It enabled us to build a shared understanding of the risks and how we would manage them.It gave us a clear picture of the controls (or barriers) we needed to have in place, allowed us to leverage our existing information security management system for many of these controls and map out ownership of each control.
It provided the single page diagram that enabled the short but productive conversations I had with senior stakeholders, enabling me to give them comfort that we had taken a structured approach to assessing the risks.Indeed when I presented the final paper to the Board, the consensus was that a decision to adopt the Cloud (in a controlled manner) was a "no brainer".
We have gone on to present the Swiss Cheese Model to our clients who are considering adopting our Cloud enabled services as a means of helping them to understand the risks and how we have addressed them. It has been equally successful in this context.
If you would like a free copy of the Swiss Cheese Model poster, released under a Creative Commons Licence, containing descriptions of all the undesired outcomes, threats, and barriers, please go here.
Part 2 in this series is a deep dive into the Swiss Cheese Model.